windows 防火墙日志_如何使用Windows防火墙日志跟踪防火墙活动

windows 防火墙日志
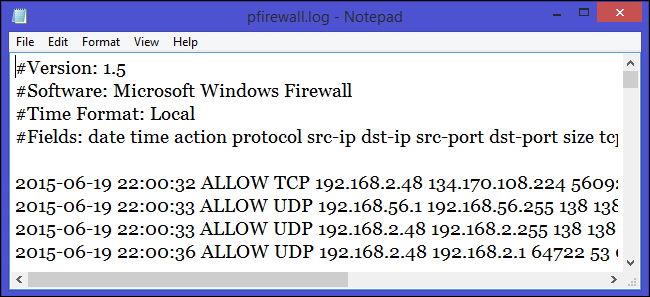
In the process of filtering Internet traffic, all firewalls have some type of logging feature that documents how the firewall handled various types of traffic. These logs can provide valuable information like source and destination IP addresses, port numbers, and protocols. You can also use the Windows Firewall log file to monitor TCP and UDP connections and packets that are blocked by the firewall.
在过滤Internet流量的过程中,所有防火墙都具有某种类型的日志记录功能,该功能记录了防火墙如何处理各种类型的流量。 这些日志可以提供有价值的信息,例如源和目标IP地址,端口号和协议。 您还可以使用Windows防火墙日志文件来监视TCP和UDP连接以及被防火墙阻止的数据包。
为什么和何时使用防火墙日志记录- 验证新添加的防火墙规则是否正常运行,或者如果它们未能按预期运行,则对其进行调试。
- 确定Windows防火墙是否是应用程序失败的原因-使用防火墙日志记录功能,您可以检查禁用的端口开放,动态端口开放,使用推送和紧急标志分析丢弃的数据包以及分析发送路径上的丢弃的数据包。
- 帮助和识别恶意活动-使用防火墙日志记录功能,您可以检查网络内是否发生了任何恶意活动,尽管您必须记住它没有提供跟踪活动来源所需的信息。
- 如果您发现反复尝试从一个IP地址(或一组IP地址)访问防火墙和/或其他高配置系统失败,那么您可能需要编写一条规则来删除该IP空间中的所有连接(请确保IP地址没有被欺骗)。
- 来自内部服务器(例如Web服务器)的传出连接可能表明某人正在使用您的系统对其他网络上的计算机发起攻击。
如何生成日志文件
(Why and When Firewall Logging is Useful- To verify if newly added firewall rules work properly or to debug them if they do not work as expected.
- To determine if Windows Firewall is the cause of application failures — With the Firewall logging feature you can check for disabled port openings, dynamic port openings, analyze dropped packets with push and urgent flags and analyze dropped packets on the send path.
- To help and identify malicious activity — With the Firewall logging feature you can check if any malicious activity is occurring within your network or not, although you must remember it does not provide the information needed to track down the source of the activity.
- If you notice repeated unsuccessful attempts to access your firewall and/or other high profile systems from one IP address (or group of IP addresses), then you might want to write a rule to drop all connections from that IP space (making sure that the IP address isn’t being spoofed).
- Outgoing connections coming from internal servers such as Web servers could be an indication that someone is using your system to launch attacks against computers located on other networks.
How to Generate the Log File
)By default, the log file is disabled, which means that no information is written to the log file. To create a log file press “Win key + R” to open the Run box. Type “wf.msc” and press Enter. The “Windows Firewall with Advanced Security” screen appears. On the right side of the screen, click “Properties.”
默认情况下,日志文件是禁用的,这意味着没有信息写入日志文件。 要创建日志文件,请按“ Win键+ R”打开“运行”框。 输入“ wf.msc”,然后按Enter。 出现“具有高级安全性的Windows防火墙”屏幕。 在屏幕右侧,点击“属性”。
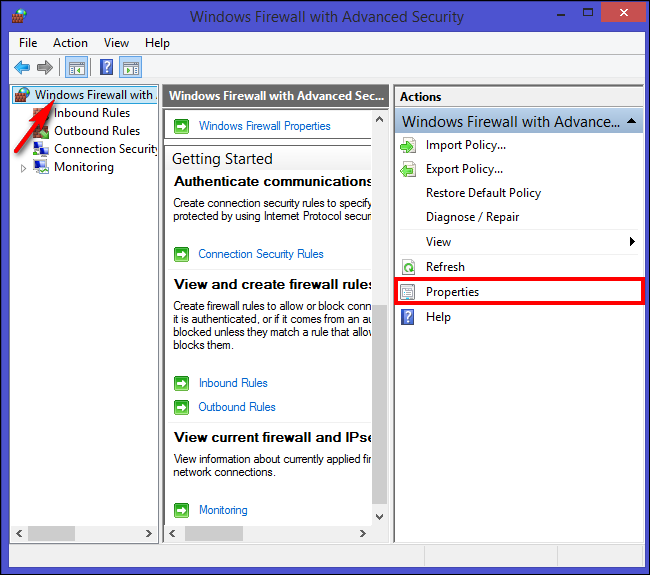
A new dialog box appears. Now click the “Private Profile” tab and select “Customize” in the “Logging Section.”
出现一个新对话框。 现在,单击“私人配置文件”选项卡,然后在“日志记录”部分中选择“自定义”。
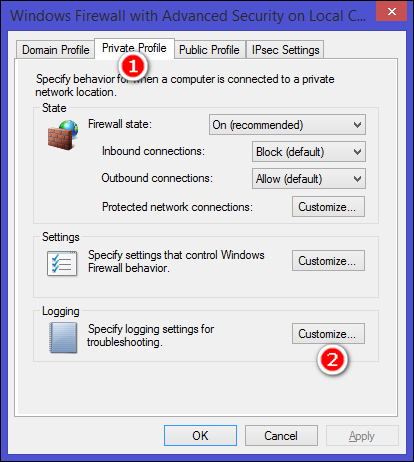
A new window opens and from that screen choose your maximum log size, location, and whether to log only dropped packets, successful connection or both. A dropped packet is a packet that Windows Firewall has blocked. A successful connection refers both to incoming connections as well as any connection you have made over the Internet, but it doesn’t always mean that an intruder has successfully connected to your computer.
将打开一个新窗口,并从该屏幕中选择最大日志大小,位置以及是否仅记录丢弃的数据包,成功连接还是同时记录两者。 丢弃的数据包是Windows防火墙已阻止的数据包。 成功的连接既指传入连接,也指您通过Internet进行的任何连接,但这并不总是意味着入侵者已成功连接到您的计算机。
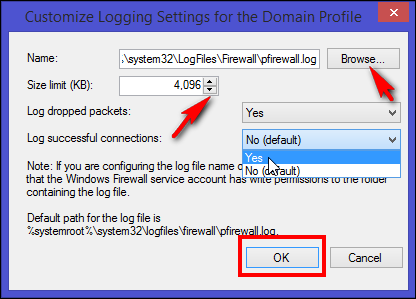
By default, Windows Firewall writes log entries to %SystemRoot%\System32\LogFiles\Firewall\Pfirewall.log and stores only the last 4 MB of data. In most production environments, this log will constantly write to your hard disk, and if you change the size limit of the log file (to log activity over a long period of time) then it may cause a performance impact. For this reason, you should enable logging only when actively troubleshooting a problem and then immediately disable logging when you’re finished.
默认情况下,Windows防火墙将日志条目写入%SystemRoot%\System32\LogFiles\Firewall\Pfirewall.log ,仅存储最后4 MB的数据。 在大多数生产环境中,此日志将不断写入硬盘,如果您更改日志文件的大小限制(以长时间记录活动),则可能会对性能造成影响。 因此,仅应在主动对问题进行故障排除时启用日志记录,然后在完成后立即禁用日志记录。
Next, click the “Public Profile” tab and repeat the same steps you did for “Private Profile” tab. You’ve now turned on the log for both private and public network connections. The log file will be created in a W3C extended log format (.log) that you can examine with a text editor of your choice or import them into a spreadsheet. A single log file can contain thousands of text entries, so if you are reading them through Notepad then disable word wrapping to preserve the column formatting. If you are viewing the log file in a spreadsheet then all the fields will be logically displayed in columns for easier analysis.
接下来,单击“公共配置文件”选项卡,然后重复执行与“私人配置文件”选项卡相同的步骤。 现在,您已经打开了专用和公用网络连接的日志。 日志文件将以W3C扩展日志格式(.log)创建,您可以使用所选的文本编辑器进行检查,也可以将其导入电子表格中。 一个日志文件可以包含数千个文本条目,因此,如果您通过记事本读取它们,则禁用自动换行以保留列格式。 如果您正在电子表格中查看日志文件,则所有字段将在逻辑上显示在列中,以便于分析。
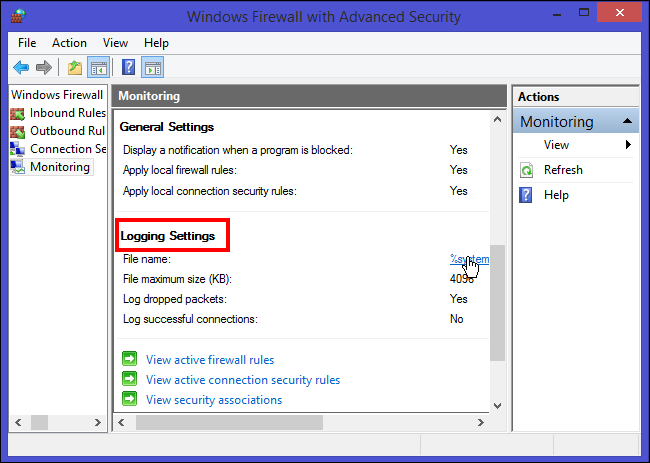
On the main “Windows Firewall with Advanced Security” screen, scroll down until you see the “Monitoring” link. In the Details pane, under “Logging Settings”, click the file path next to “File Name.” The log opens in Notepad.
在“具有高级安全性的Windows防火墙”主屏幕上,向下滚动,直到看到“监视”链接。 在“详细信息”窗格中的“日志记录设置”下,单击“文件名”旁边的文件路径。 日志在记事本中打开。
解释Windows防火墙日志 (Interpreting the Windows Firewall log )
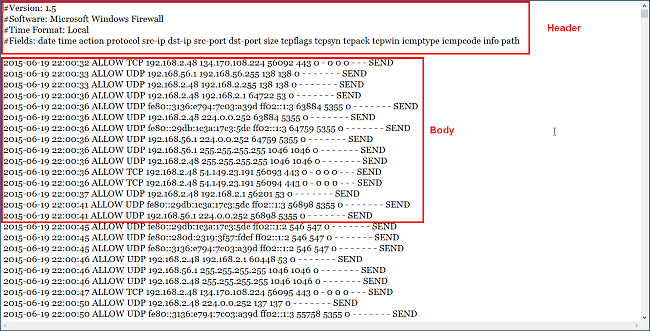
The Windows Firewall security log contains two sections. The header provides static, descriptive information about the version of the log, and the fields available. The body of the log is the compiled data that is entered as a result of traffic that tries to cross the firewall. It is a dynamic list, and new entries keep appearing at the bottom of the log. The fields are written from left to right across the page. The (-) is used when there is no entry available for the field.
Windows防火墙安全日志包含两个部分。 标头提供有关日志版本以及可用字段的静态描述性信息。 日志的主体是由于试图通过防火墙的通信而输入的已编译数据。 这是一个动态列表,新条目始终出现在日志的底部。 这些字段在页面上从左到右书写。 没有该字段的可用条目时使用(-)。
According to the Microsoft Technet documentation the header of the log file contains:
根据Microsoft Technet文档,日志文件的标题包含:
Version — Displays which version of the Windows Firewall security log is installed. Software — Displays the name of the software creating the log. Time — Indicates that all the timestamp information in the log are in local time. Fields — Displays a list of fields that are available for security log entries, if data is available.
版本—显示安装的Windows防火墙安全日志的版本。 软件—显示创建日志的软件的名称。 时间-表示日志中的所有时间戳信息均以本地时间表示。 字段-如果数据可用,则显示可用于安全日志条目的字段列表。
While the body of the log file contains:
虽然日志文件的正文包含:
date — The date field identifies the date in the format YYYY-MM-DD. time — The local time is displayed in the log file using the format HH:MM:SS. The hours are referenced in 24-hour format. action — As the firewall processes traffic, certain actions are recorded. The logged actions are DROP for dropping a connection, OPEN for opening a connection, CLOSE for closing a connection, OPEN-INBOUND for an inbound session opened to the local computer, and INFO-EVENTS-LOST for events processed by the Windows Firewall, but were not recorded in the security log. protocol — The protocol used such as TCP, UDP, or ICMP. src-ip — Displays the source IP address (the IP address of the computer attempting to establish communication). dst-ip — Displays the destination IP address of a connection attempt. src-port — The port number on the sending computer from which the connection was attempted. dst-port — The port to which the sending computer was trying to make a connection. size — Displays the packet size in bytes. tcpflags — Information about TCP control flags in TCP headers. tcpsyn — Displays the TCP sequence number in the packet. tcpack — Displays the TCP acknowledgement number in the packet. tcpwin — Displays the TCP window size, in bytes, in the packet. icmptype — Information about the ICMP messages. icmpcode — Information about the ICMP messages. info — Displays an entry that depends on the type of action that occurred. path — Displays the direction of the communication. The options available are SEND, RECEIVE, FORWARD, and UNKNOWN.
date —日期字段以YYYY-MM-DD格式标识日期。 time —当地时间以格式HH:MM:SS显示在日志文件中。 这些小时以24小时格式引用。 操作—当防火墙处理流量时,会记录某些操作。 记录的操作包括:DROP(用于断开连接),OPEN(用于断开连接),CLOSE(用于断开连接),OPEN-INBOUND(对于向本地计算机打开的入站会话)和INFO-EVENTS-LOST(对于由Windows防火墙处理的事件),但是没有记录在安全日志中。 协议—使用的协议,例如TCP,UDP或ICMP。 src-ip —显示源IP地址(尝试建立通信的计算机的IP地址)。 dst-ip —显示连接尝试的目标IP地址。 src-port —尝试从中进行连接的发送计算机上的端口号。 dst-port —发送计算机尝试建立连接的端口。 size —显示数据包大小(以字节为单位)。 tcpflags —有关TCP标头中的TCP控制标志的信息。 tcpsyn —显示数据包中的TCP序列号。 tcpack —显示数据包中的TCP确认号。 tcpwin —显示数据包中的TCP窗口大小(以字节为单位)。 icmptype —有关ICMP消息的信息。 icmpcode —有关ICMP消息的信息。 info —显示一个条目,该条目取决于发生的操作的类型。 路径—显示通信方向。 可用的选项为SEND,RECEIVE,FORWARD和UNKNOWN。
As you notice, the log entry is indeed big and may have up to 17 pieces of information associated with each event. However, only the first eight pieces of information are important for general analysis. With the details in your hand now you can analyze the information for malicious activity or debug application failures.
如您所见,日志条目确实很大,并且每个事件可能包含多达17条信息。 但是,只有前八条信息对一般分析很重要。 现在,有了您的详细信息,您就可以分析信息以进行恶意活动或调试应用程序故障。
If you suspect any malicious activity, then open the log file in Notepad and filter all the log entries with DROP in the action field and note whether the destination IP address ends with a number other than 255. If you find many such entries, then take a note of the destination IP addresses of the packets. Once you have finished troubleshooting the problem, you can disable the firewall logging.
如果您怀疑有任何恶意活动,请在记事本中打开日志文件,并在操作字段中使用DROP过滤所有日志条目,并注意目标IP地址是否以255以外的数字结尾。如果找到许多此类条目,则采用数据包的目标IP地址的注释。 对问题进行故障排除后,可以禁用防火墙日志记录。
Troubleshooting network problems can be quite daunting at times and a recommended good practice when troubleshooting Windows Firewall is to enable the native logs. Although the Windows Firewall log file is not useful for analyzing the overall security of your network, it still remains a good practice if you want to monitor what is happening behind the scenes.
对网络问题进行故障排除有时会令人生畏,在对Windows防火墙进行故障排除时,建议的良好做法是启用本机日志。 尽管Windows防火墙日志文件对于分析网络的整体安全性没有用,但是如果您要监视幕后发生的情况,它仍然是一个好习惯。
翻译自: https://www.howtogeek.com/220204/how-to-track-firewall-activity-with-the-windows-firewall-log/
windows 防火墙日志
